Electronic and digital signatures
Electronic signatures and digital signatures should be considered on an equal level to handwritten signatures (‘wet ink’).
The requirements that need to be fulfilled depend on the extent of the binding force that is to be achieved and so depend on the document that is to be signed.
This article explains:
- when manufacturers require a signature
- under which circumstances documents may be signed electronically
- what type of electronic signature is required
- what the difference is between an electronic signature and a digital signature
- how electronic signing can be put into practice.
1. When is a signature needed?
a) Medical Devices Directive MDD
The MDD does not mention the word ‘signature’. However, in Annex II (EC Declaration of Conformity) it does say:
‘The manufacturer must affix the CE marking in accordance with Article 17 and draw up a written
declaration of conformity.’#MDD, Annex II
The authorities and notified bodies understand this to mean that this declaration requires a signature.
b) Medical Device Regulation MDR
The MDR explicitly demands signatures, for example, in Annex IV on the EU Declaration of Conformity:
‘The EU declaration of conformity shall contain all of the following information: [...] Place and date of issue of the declaration, name and function of the person who signed it as well as an indication for, and on behalf of whom, that person signed, signature.’
MDR, Annex IV
Manufacturers must also provide a signature when they request a notified body to carry out a conformity assessment. (Annex VII Requirements to be met by notified bodies).
In the case of clinical investigations, the MDR requires the signatures of the ‘principal investigators’.
c) ISO 13485:2016
DIN EN ISO 13485:2016 does not mention the term ‘signature’. However, in Section 4.2.4 (Control of Documents) it demands that:
‘A documented procedure shall define the controls needed to:
a) review and approvedocuments for adequacy prior to issue; [...]’DIN EN ISO 13485:2016, Section 4.2.4
With this the manufacturers are obliged to prove that:
- documents are written, reviewed and approved
- this occurs in this order
- it is not the same person who writes, reviews and approves each document
- approval takes place prior to issue.
These requirements can only be met by assigning the document and tasks to a different person and date for each task. This assignation takes place by means of a signature.
With this signature the individuals involved express the following:
- Authorship: ‘I am responsible for the contents and consider them to be correct’
- Review: ‘I have reviewed the contents according to established criteria and they meet the criteria’
- Approval/release: ‘The contents can be used in the further process (and I have the authority to decide this)’
Further information
Read more here on the subject of Document releases and the four-eyes principle.
These requirements are comprehensible: creating a system specification before the user requirements have been recorded and documented more often than not does not make much sense. Before a product is reproduced in the production process, the design must be tested.
d) Summary
From this, we can conclude that:
- Manufacturers must create documents such as technical documentation and the declaration of conformity;
- Manufacturers must sign these documents;
- With their signature the manufacturers declare product conformity in the case of the declaration of conformity (and thus the safety of the product) and process conformity in the case of the technical documentation.
2. When are electronic signatures needed?
There is (as yet) no obligation to create and deliver documents in a digital format. However, there is increasing pressure from the authorities and notified bodies to do this. Standardised electronic formats like CDISC in the case of clinical trials are to some extent the single most efficient form of communication.
As soon as manufacturers create electronic documents instead of paper documents, they must replace handwritten signatures with electronic or digital signatures.
3. When are electronic signatures allowed?
a) In Germany/Europe: BGB, VDG, eIDAS
In §126 Written form, the German Civil Code (BGB) explicitly gives permission to replace handwritten signatures with electronic signatures:
‘...(3) Written form may be replaced by electronic form, unless the statute leads to a different conclusion. ...’
BGB, §126
In the case of signatures prescribed by statute, the BGB sets the bar a bit higher:
‘(1) If electronic form is to replace the written form prescribed by statute, the issuer of the declaration must add his name to it and provide the electronic document with a qualified electronic signature in accordance with the Electronic Signature Act [Signaturgesetz].’
BGB §126a
What exactly a ‘qualified electronic signature’ consists of is regulated by the German Trust Services Act (VDG) (previously the Signature Act), which transposes the EU regulationeIDAS (former Signatures Directive) (see Fig. 1).
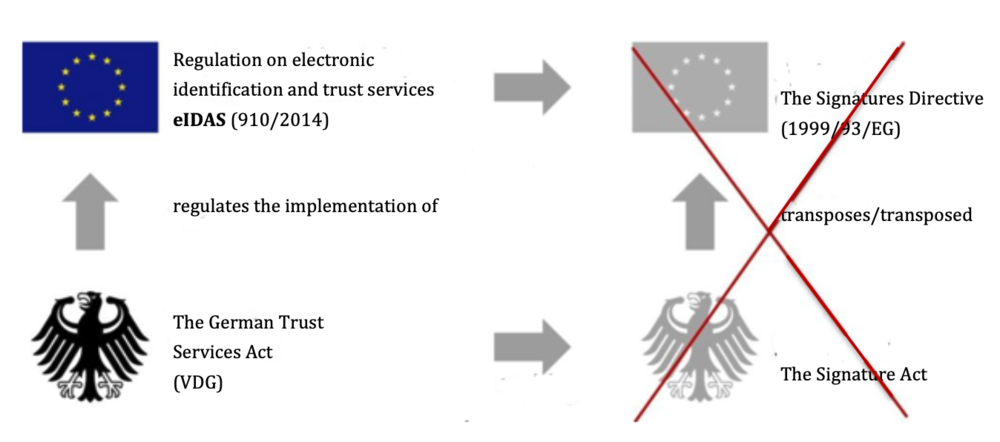
Fig. 1: The German Trust Services Act (VDG) transposes the EU regulation eIDAS and repeals the Signature Act, which transposed the former EU Signatures Directives.
b) USA – FDA: 21 CFR part 11
The FDA also allows written signatures to be replaced by electronic signatures. The signatures and the signed documents must then meet the requirements of 21 CFR part 11.
The requirements of this administrative law only apply to companies that communicate with the FDA or that have to present documents to the authorities, e.g. during an inspection.
Further information
Read more on the subject here 21 CFR part 11.
4. What types of electronic signatures are there?
The EU regulation on electronic identification and trust services (eIDAS (910/2014) for short) differentiates between three types of electronic signatures:
- Electronic signature
- Advanced electronic signature
- Qualified electronic signature
a) Electronic signature
The eIDAS defines an electronic signature as follows:
Definition: electronic signature
‘[...] data in electronic form which is attached to or logically associated with other data in electronic form and which is used by the signatory to sign.’
‘[...] data in electronic form which is attached to or logically associated with other data in electronic form and which is used by the signatory to sign.’
Source: eIDAS
The inclusion of a scanned signature in a document is an example of an electronic signature. The signature in an email is also an electronic signature.
This signature is the weakest form of proof as it cannot be guaranteed that the person themselves have attached or logically associated these data, nor can the time that it was attached be tracked.
b) Advanced electronic signature
On the next level is the advanced electronic signature.
Definition: advanced electronic signature
Electronic signatures that:
a.) are uniquely linked to the signatory
b.) enable identification of the signatory
c.) are ‘created using electronic signature creation data that the signatory can, with a high level of confidence, use under his sole control’
d.) ‘are linked to the data signed therewith in such a way that any subsequent change in the data is detectable.’
Source: eIDAS
Examples of this type of electronic signature are version control systems like SVN or Git:
When the user clicks on ‘Commit’, the name of the person and the time are also saved every time. The person can be identified by their username and password. On an organisational level it can be guaranteed that only the individual themselves has these credentials. Finally, check sums ensure that any subsequent changes to the data do not go unnoticed. This is precisely what version control systems are designed for.
But even electronic signatures can be manipulated:
- If the organisational measures are ineffective, it would be possible for a second person to use the same name or to gain access to the access data and thus the identity of the first person.
- By changing the time on the version control system, the time stamp can be manipulated.
To minimise these drawbacks, a higher ‘integrity level’ is required: the qualified electronic signature.
c) Qualified electronic signature
This type of signature is also defined under the eIDAS:
Definition: qualified electronic signature
‘An advanced electronic signature that is
a.) created by a qualified electronic signature creation device, and
b.) which is based on a qualified certificate for electronic signatures’
Source: eIDAS
In Annex II the regulation goes on to say:
’(3) Generating or managing electronic signature creation data on behalf of the signatory may only be done by a qualified trust service provider.’
Source: eIDAS
These service providers include:
- The German Federal Employment Agency
- Bundesnotarkammer (body representing German civil law notaries)
- Deutsche Post AG
- D-Trust GmbH
- Deutscher Sparkassen Verlag GmbH
- Deutsche Telekom AG
- DGN Deutsches Gesundheitsnetz Service GmbH
- medisign GmbH
5. What type of electronic signature is needed?
a) Risk-based approach of ISO 13485:2016
ISO 13485:2016 says that processes and the validation of computer systems should be risk-based. This risk-based approach also applies when selecting the type of electronic signature.
Where human lives are involved (> product conformity), a selection is made on the highest level. When it is a matter of proving that the procedure specifications have been followed (> process conformity), an advanced electronic signature should suffice.
In other words: manufacturers should sign a declaration of conformity by hand (‘wet ink’) or using a qualified electronic signature. In the case of specifications, test reports, etc. an advanced electronic signature is sufficient.
b) Legal requirements in Europe
The eIDAS explicitly makes it plain:
‘(1) An electronic signature shall not be denied legal effect and admissibility as evidence in legal proceedings solely on the grounds that it is in an electronic form or that it does not meet the requirements for qualified electronic signatures.’
eIDAS
c) Legal requirements in the USA
21 CFR part 11 differentiates between the electronic signature and the digital signature:
‘(5) Digital signature means an electronic signature based upon cryptographic methods of originator authentication, computed by using a set of rules and a set of parameters such that the identity of the signer and the integrity of the data can be verified.’
‘(7) Electronic signature means a computer data compilation of any symbol or series of symbols executed, adopted, or authorized by an individual to be the legally binding equivalent of the individual’s handwritten signature.’
21 CFR part 11
Here, the electronic signature corresponds to the electronic signature according to eIDAS and the digital signature at least to the advanced electronic signature.
The FDA does not make any demands that could only be met by a qualified electronic signature. It requires:
- that falsification must be detected (11.10)
- appropriate standards for digital signatures to be able to guarantee the authenticity, integrity and confidentiality of records (11.30)
- a guarantee that signatures cannot be excised or transferred to other documents (11.70)
- that if a person wishes to provide several electronic signatures, they must first login with all data (typically username and password), then with at least one component for each individual procedure (typically password or PIN) (11.200)
- a guarantee that collaboration of two or more individuals is required to forge the electronic signature of a third party. (11.200)
- on the electronically signed document the FDA expects the name of the signatory (printed, no image/scan of the signature), date and time of signing and what is confirmed by the signature (authorship, review, approval) (11.50).
Conclusion: none of these requirements make it compulsory to use qualified electronic signatures. An advanced electronic signature with a validated system and appropriate organisational measures are sufficient.
6. How (with which tools) is a digital signature created?
The Johner Institute recommends the use of tools for creating digital signatures. The type of tool that is appropriate depends on the manufacturer’s way of working:
- If manufacturers work above all using documents (e.g. with Word), Adobe and Microsoft products (e.g. Word) alone or with plugins are enough to meet the technical requirements of an advanced electronic signature.
- The Johner Institute creates most documents in Markdown format and uses Git as a version control tool. Through appropriate organisational measures (e.g. branching and merging specifications) the requirements of an advanced electronic signature can be met.
- It is very smart to opt for tools that look after the contents of the documents in a database such as ALM tools, e.g. those by Medsoto (MedPack, RiskPack and DocuPack). These products already have built-in mechanisms, such as PIN approval confirmation, to generate advanced electronic signatures that are legally compliant.
The signing of declarations of conformity does not normally justify the effort of setting up a system with which qualified electronic systems can be created.
7. How does digital signing actually work?
a) Digital signature: what does it have to do with hash values, e.g. MD5 and SHA?
First of all, a hash value is calculated from the document. The hash value is a character string (currently usually 254 bits or longer) and is equivalent to the document’s fingerprint. Any even slight change to the document will lead to another hash value in an inspection. It is (with realistic effort) not possible to draw conclusions about the contents of the document from the hash value.
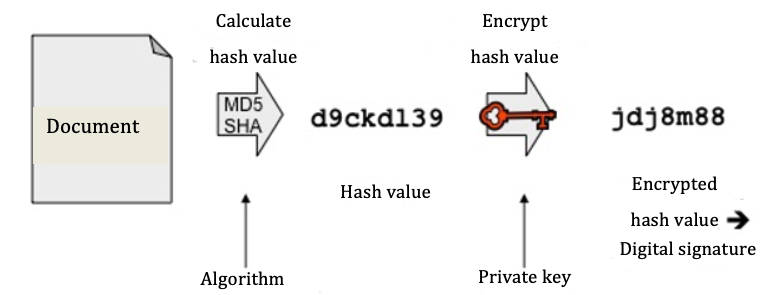
Fig. 2: Creating a digital signature
Processes (algorithms) that are well-known and still used to calculate this value today are MD5 (128 bits), SHA-256, and SHA-512. Every year, the BSI (Federal Office for Information Security) issues recommendations in this regard, which are agreed upon with experts.
Typical lengths for a digital signature are 1536 bits and more. As hash algorithms create clearly shorter character strings, these are then filled out with special characters. This procedure is called padding.
b) Encrypting, RSA and digital signatures
Up to this point, neither the original document nor its hash value can be assigned to an author. This takes place in the second step, whereby the (padded) hash value is linked to a signature by a signature process using the author's private key. Widely used, asymmetrical processes for this are RSA or DSA.
Please note: for signature purposes the hash value and not the whole document is linked with the key, as for this purpose it is not the contents of the document that should be concealed but ‘simply’ its integrity that must be guaranteed. So the hash value is an important component of the digital signature.
The BSI analyses the safety of the recommended signature and encryption processes on a yearly basis. A signature based on RSA or DSA with a length of 1728 bits was seen to be safe until 2010. Since then, at least 2048 bits are required.
c) Key, certificate and certification body
Certificates prove that the key can truly be assigned to the author in a trustworthy manner. They are issued by trust centres (certification bodies), are signed by the centre (and thus have integrity) and, alongside the name of the author and the expiration date, also contain their public key. The public and private key thereby form a pair. Whilst the public key is created from the private key, this is not possible the other way round, that is, the private key cannot be ascertained from the public key. The safety of the procedure is based on such a ‘one-way function’.
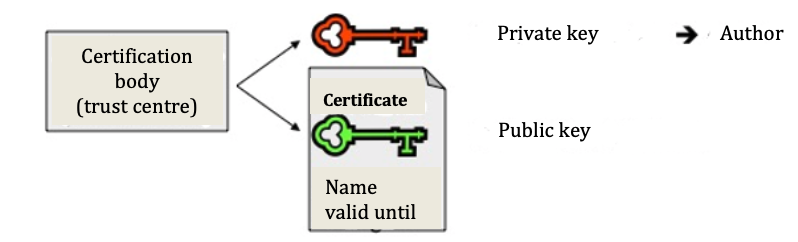
Fig. 3: Creating a private key and certificate with a public key
With the public key from the certificate of the potential sender, the recipient can verify the digital signature attached to the document and thus check the correctness of the data on the author (author or sender). In doing so the saved hash value will also be visible. The recipient then compares the encrypted value with the hash value, which they themselves have calculated using the same algorithm. If both coincide, the recipient knows for sure that the document has not been modified and so is authentic.
8. Conclusion/Summary
a) Avoid unnecessary effort
The effort that some companies go to in order to meet alleged legal requirements bears unusual fruit: electronic documents are created; they’re printed out; then they’re signed and scanned back on to the computer; this scan then goes to be filed in the document management system, which with a complex authorisation process ensures that the individuals working with it can be identified.
It is easy to affect the efficiency of the process with unreasonably high requirements and thus bring the whole company to a standstill.
b) Act on the basis of risk
The signature level should be selected based on risk: the Johner Institute recommends a qualified electronic signature above all for declarations of conformity (when it’s a matter of life or death) and external legal transactions. In the other cases an advanced electronic signature is sufficient, which you can create yourself with many tools, together with appropriate organisational measures.
Many auditors make demands concerning electronic signatures for which there is no legal basis. These auditors often act inconsistently as they insist on handwritten signatures but not on a specimen signature.
But despite all the enthusiasm for electronic signatures and digitalisation, isn’t it also a ceremonial act to sign a declaration of conformity with proper fountain pen and to confirm that the product is safe and benefits patients?


